Network & Passwords Sniffer through Wireshark
Computers communicate using networks. These networks could be on a local area network LAN or exposed to the internet. Network Sniffers are programs that capture low-level package data that is transmitted over a network. An attacker can analyze this information to discover valuable information such as user ids and passwords.
What is network sniffing?
Network sniffing is the process of intercepting data packets sent over a network. This can be done by the specialized software program or hardware equipment. Sniffing can be used to;
- Capture sensitive data such as login credentials
- Eavesdrop on chat messages
- Capture files have been transmitted over a network
The following are protocols that are vulnerable to sniffing
- Telnet
- Rlogin
- HTTP
- SMTP
- NNTP
- POP
- FTP
- IMAP
The above protocols are vulnerable if login details are sent in plain text.
Hacking Activity: Sniff network traffic
In this practical scenario, we are going to use Wireshark to sniff data packets as they are transmitted over HTTP protocol. For this example, we will sniff the network using Wireshark, then login to a web application that does not use secure communication. We will login to a web application on http://www.techpanda.org/
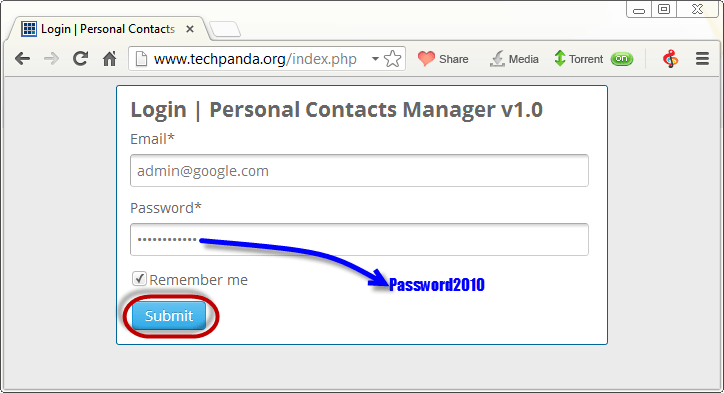
The login address is admin@google.com, and the password is Password2010.
Sniffing the network using Wireshark
The illustration below shows you the steps that you will carry out to complete this exercise without confusion
Download Wireshark from this link http://www.wireshark.org/download.html
- Open Wireshark
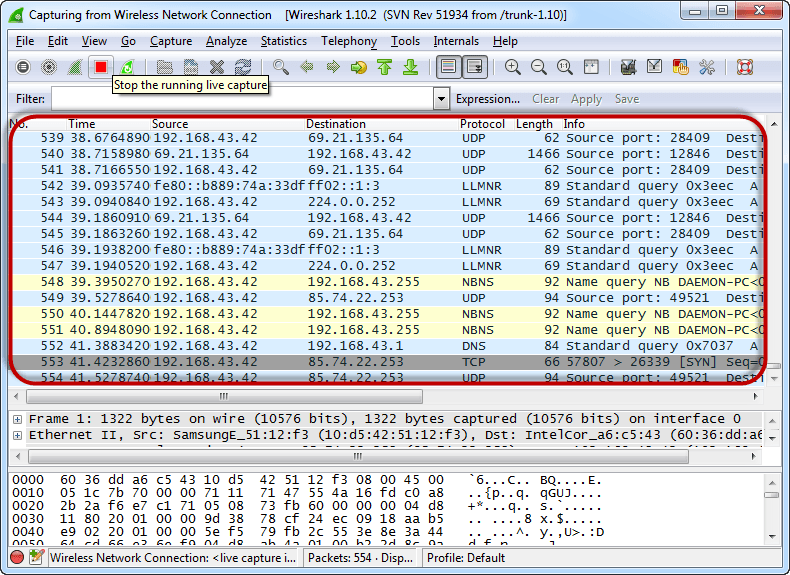
- You will get the following screen
- Select the network interface you want to sniff. Note for this demonstration, we are using a wireless network connection. If you are on a local area network, then you should select the local area network interface.
- Click on start button as shown above
- Open your web browser and type in http://www.techpanda.org/
- The login email is admin@google.com and the password is Password2010
- Click on submit button
- A successful login should give you the following dashboard
- Go back to Wireshark and stop the live capture
- Filter for HTTP protocol results only using the filter textbox
- Locate the Info column and look for entries with the HTTP verb POST and click on it
- Just below the log entries, there is a panel with a summary of captured data. Look for the summary that says Line-based text data: application/x-www-form-urlencoded
- You should be able to view the plaintext values of all the POST variables submitted to the server via HTTP protocol.








good sir
ReplyDelete